Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertextThe keys may be identical or there may be a simple transformation to go between the two keys. Finally they show how to use RSA in a typical program using the appropriate.

What Is Symmetric Key Cryptography Encryption Security Wiki
One of the first popular symmetric cryptography algorithms was RSA.

Was one of the first popular symmetric cryptography algorithms rsa. Generating Public Key. Pts one of the first popular symmetric cryptography. Not be a factor of n.
This is because of asymmetric encryptions creation and exchange of the two keys versus the single one in private or symmetric encryption. Lets compare a few popular algorithms that have historical or current significance in the era of modern encryption. What cryptographic method first proposed in the mid-1980s makes use of sloping curves instead of large prime numbers.
Group of answer choices True False Flag this Question Question 4 05 pts. Now First part of the Public key. The authors of NET Security and Cryptography also examine how asymmetric algorithms work at a conceptual level and also provide a detailed analysis of RSA which is currently the most popular asymmetric algorithm.
Published in 1976 the Diffie-Hellman algorithm was one of. RSA is a term quite commonly used when it comes to cryptography. Let us learn the mechanism behind RSA algorithm.
Learn how asymmetric algorithms solve the shortcomings of symmetric algorithms. Asked Feb 14 2019 in Computer Science Information Technology by sciencefun networking-and-telecommunications. Asymmetric actually means that it works on two different keys ie Public Key and Private Key.
The Rivest Shamir Adelman RSA algorithm is the most popular symmetric key algorithm. Select two prime nos. The denotations of their public and private keys are as follow.
The simplest type of stream cipher one in which one letter or character is exchanged for another is known as what. Public-A and Private-A for Alice Public-B and. What type of cipher takes one character and replaces it with one character working one character at a time.
The keys in practice represent a shared secret between two or more parties that can be used to maintain a private information link. The RSA algorithm was developed by Ron Rivest Adi Shamir and Len Adelman at MIT 25 in 1977. Asymmetric encryption algorithms also known as digital signature schemes form the basis of secure communication using public keys and private keys.
RC2 is a 64-bit block cipher that supports a key length of up to 128 bits although it was initially only approved for US export with a 40-bit key. One of the first popular symmetric cryptography algorithms was RSA. But e Must be.
It is based on the idea of prime factorization of integers. It was invented by mathematicians named Rivest Shamir and Adleman hence where the name RSA was derived in year 1978. Suppose P 53 and Q 59.
We also need a small exponent say e. Today RSA is the most widely used public key encryption method. The first members of the RC algorithm family RC2 and RC4 aka ARC4 or ARCFOUR were designed by Ron Rivest of RSA fame in 1987.
RSA is a modern cryptographic algorithm that encrypts and decrypts data. Question 305 pts One of the first popular symmetric cryptography algorithms was RSA. The RSA algorithm named for its creators Ron Rivest Adi Shamir and Leonard Adleman is an asymmetric algorithm used all over the world including in the Secure Sockets Layer SSL protocol which is used to secure many common transactions such as Web and e-mail traffic.
Comparatively symmetric key encryption is much faster than asymmetric techniques 8. History of RSA Encryption Introduction. N PQ 3127.
Ø RSA encryption is a 1000 times slower than typical symmetric algorithms Ø hard to remember secret key - where do you store it. 1 e Φ n Φ n is discussed below Let us now consider it to be equal. The Diffie-Hellman Key Exchange and RSA named after its inventors RivestShamirAdleman are two of the most popular encryption algorithms.
RSA was created in 1977 and is still one of. Ø typically only used for authentication then a random key and a symmetric encryption algorithm is used for subsequent communication Multicast is problematic Ø Better to authenticate using public key algorithm. RSA algorithm is asymmetric cryptography algorithm.
As the name explains that the Public Key is given to everyone and Private key is kept private.
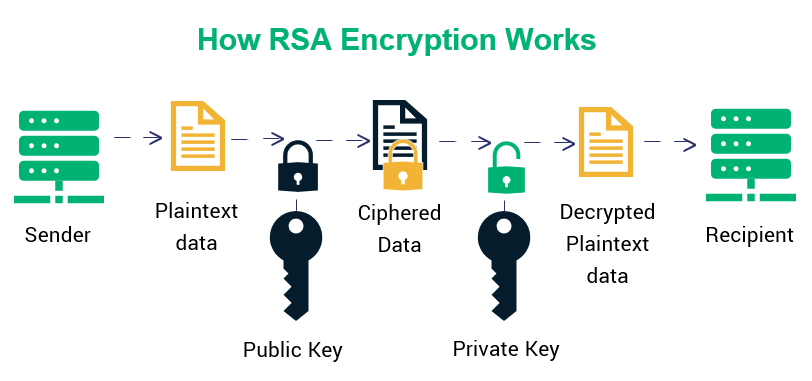
Ecdsa Vs Rsa Everything You Need To Know
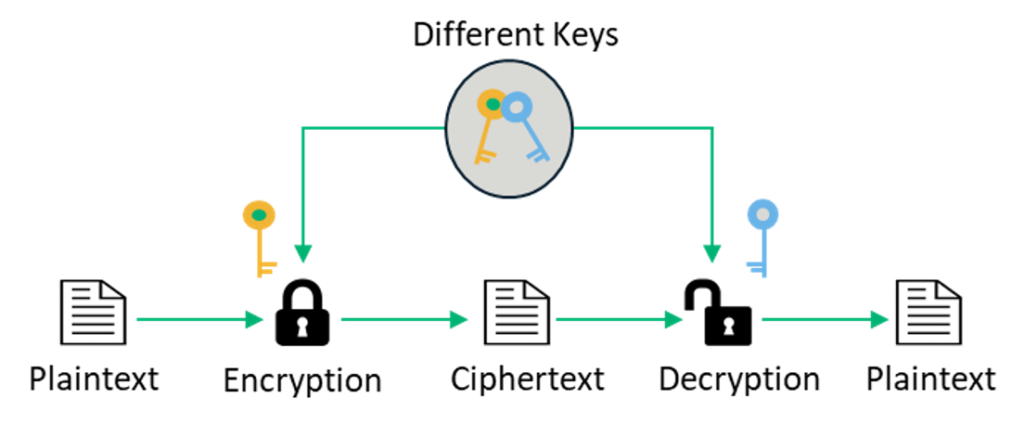
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts

Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report
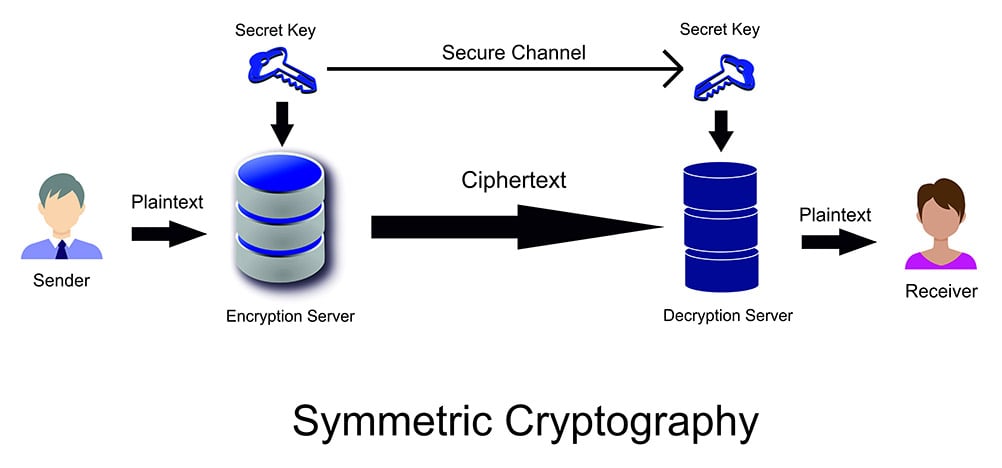
Symmetric Vs Asymmetric Encryption What S The Difference

Asymmetric Means You Re Using Two Different Keys One To Encrypt And One To Decrypt We Also Call This Public Safe Internet Cryptography Certificate Authority

Symmetric Vs Asymmetric Encryption Encryption Consulting

Si110 Asymmetric Public Key Cryptography

How Does Https Work Safe Internet Cryptography Internet Traffic