Up to 512 bits Merkle tree NLFSR it is also a keyed hash function RadioGatún. This is one of the first algorithms to gain widespread approval.
The RACE Integrity Primitives Evaluation Message Digest or RIPEMD-160 was developed in Belgium in the.
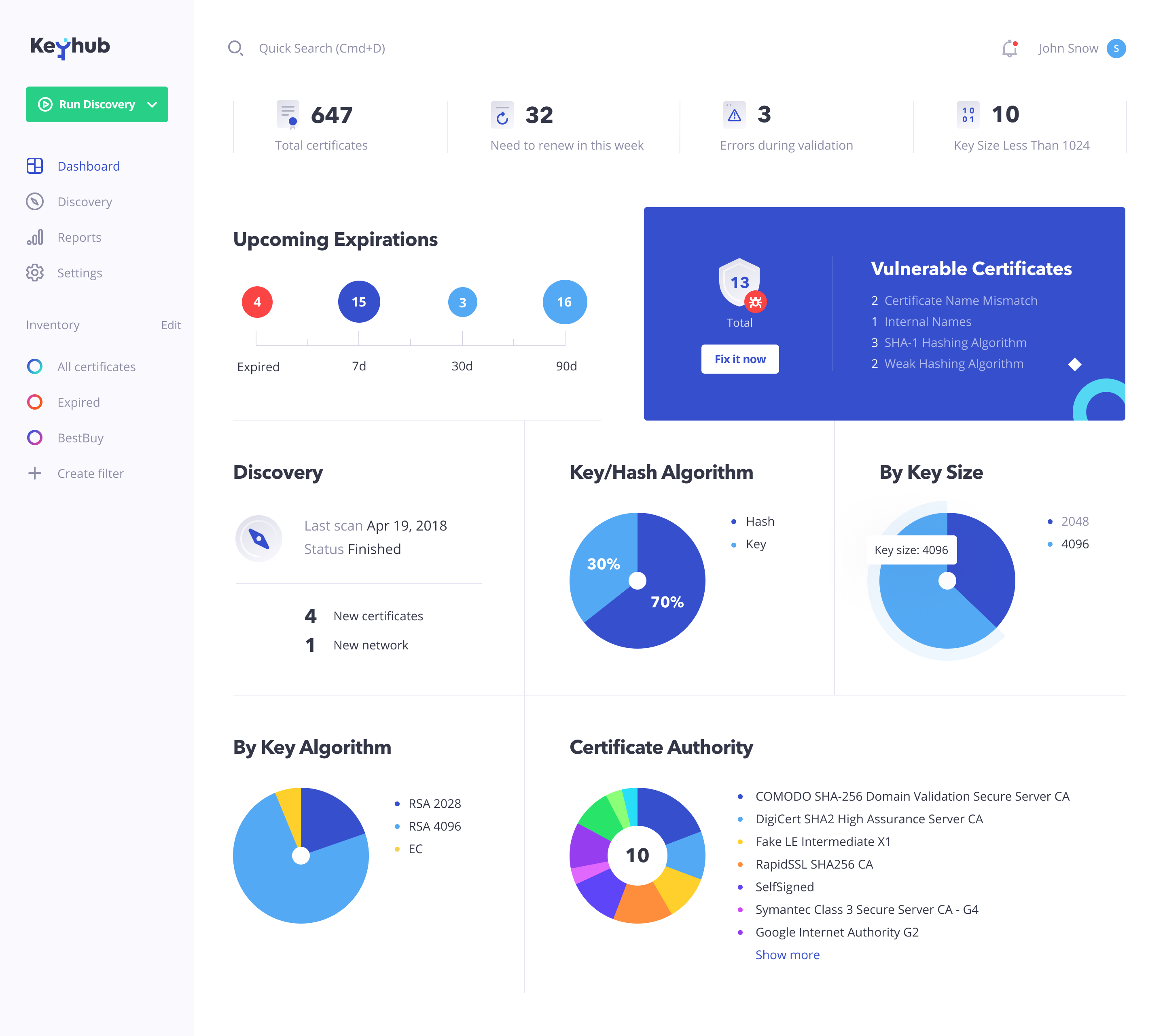
A popular hashing algorithm is. Common hashing algorithms. In cryptography the Whirlpool algorithm is one of the hash functions. SHA-1 is a popular hashing algorithm released in 1994 it was developed by NIST.
The abbreviation SHA is the Secure Hash Algorithm and 256 means that the cryptocurrency algorithm generates a 256-bit hash ie a string of 256 bits. What is a Bitcoin hash and SHA-256. Arbitrary ideal mangling function RIPEMD.
Types of Hashing Algorithms. Hashing algorithms are used extensively in cryptography for encrypting keys or messages. This prompted Rivest in 1990 to create MD4 which exploited.
Lets list them below. Message Digest 5 MD5 uses a 128-bit hash and Secure Hash Algorithm SHA uses a 60-bit hash. Hashing algorithms define the rules for how the hash is created.
The idea was to create relatively fast a digest of a message and sign that. A list of 216553 English words archive in lowercase. Merkle developed SNEFRU in 1990.
One common way of generating cryptographic hashes is to use block ciphers. Here are some of todays most well-known hashing algorithms. HAVAL is a widely popular hash function it differs from many other hash functions because it is possible for it to generate hash values in different lengths the lengths of the hashes can be 128 bits 160 bits 192 bits 224 bits or 245 bits.
It is one of the popular hashing methods out there including Message Direct MD5 and Secure Hash Function SHA1. Its based on an AES-like block. Type 4 uuid GUIDs For each corpus the number of collisions and the average time spent hashing.
I used three different key sets. Some common hash functions are MD5 which is broken and obsolete SHA-1 SHA-2 and SHA-3. If the algorithm is unsafe hackers could reverse-engineer it to reveal the original message.
Hash Algorithms Driven by the slowness of RSA in signing a message. 224 to 512 bits hash LSH. It was designed in the year 1992.
Examples of popular cryptographic hashing algorithms include MD2 MD4 MD5 and SHA-1. But theres a caveat. The slightest change in the data will result in a dramatic difference in the resulting hash values.
128 bits hash RIPEMD-128. 128 bits hash MD4. Algorithms in the.
Common hashing algorithms include. 256 to 512 bits wide-pipe MerkleDamgård construction. MD Message Digest Algorithm.
I tested some different algorithms measuring speed and number of collisions. SHA-1 is similar to MD4 and MD5 hashing algorithms and due to the fact that it is slightly more secure than MD4 MD5 it is considered as MD5s successor. By far this is one of the most used hashing algorithms in the world.
This was the origin of MD and MD2 algorithms by Ron Rivest In 1989. Here Are Some of the Popular Hashing Algorithms. 128 bits MerkleDamgård construction.
128 bits hash MD5. SHA-256 is a secure encryption algorithm that has gained popularity due to the Bitcoin code. It was many times faster than MD2.
As you can see we used the Secure Hash Function SHA-256 hashing algorithm. 128 bits hash RIPEMD-160. Its one of the widely used cryptographic hash function which relies upon the hash.
The key properties of the hash function make it reliable. Although the Message Digest algorithm 5 MD5 hashing algorithm was once one of the most popular hashing algorithms available the Secure Hash Algorithm SHA-2 and SHA-3 family of hashing algorithms is now considered the most secure because MD5 generates many collisions. There are many different types of hash algorithms such as RipeMD Tiger xxhash and more but the most common type of hashing used for file integrity checks are MD5 SHA-2 and CRC32.
There are multiple types of hashing algorithms but the most common are Message Digest 5 MD5 and Secure Hashing Algorithm SHA 1 and 2. It was designed in 1991 and at the time it was.

Syntax What Is The Difference Between And In Python Stack Overflow With Images Python

Pin By Reza Razin On Python Data Structures Startup News Java